Your virtual datacenter powered by vmware
Our virtual Switzerland data center is designed to enable you to completely manage one or multiple servers, including networking and backup without our intervention.
Our virtual secure data storage for business solution represents the functionality of a physical data center because you can have multiple servers, storage clusters, networking components, and cloud computing technologies.
However, all this enterprise infrastructure will reside in a virtual space inside our secure datacenter. Our encrypted datacenter won't require your physical presence.
Our industry-leading encryption datacenter security technology encrypts the cloud server, scrambles the data randomly, and disperses it to different secure locations.
How does it work?
Each host encrypts the disk data using the industry standard AES-256 XTS mode. Each disk will also have a different randomly generated Data Encryption Key (DEK). Each environment requests a Key Encryption Key (KEK) from the Key Management Service (KMS). Each underlying host will use the KEK to encrypt its DEK. The encrypted DEKs will be stored on disk. The host will not store the KEK on the disk itself. Find out more about our encryption standards here.
Cloud self-service web portal
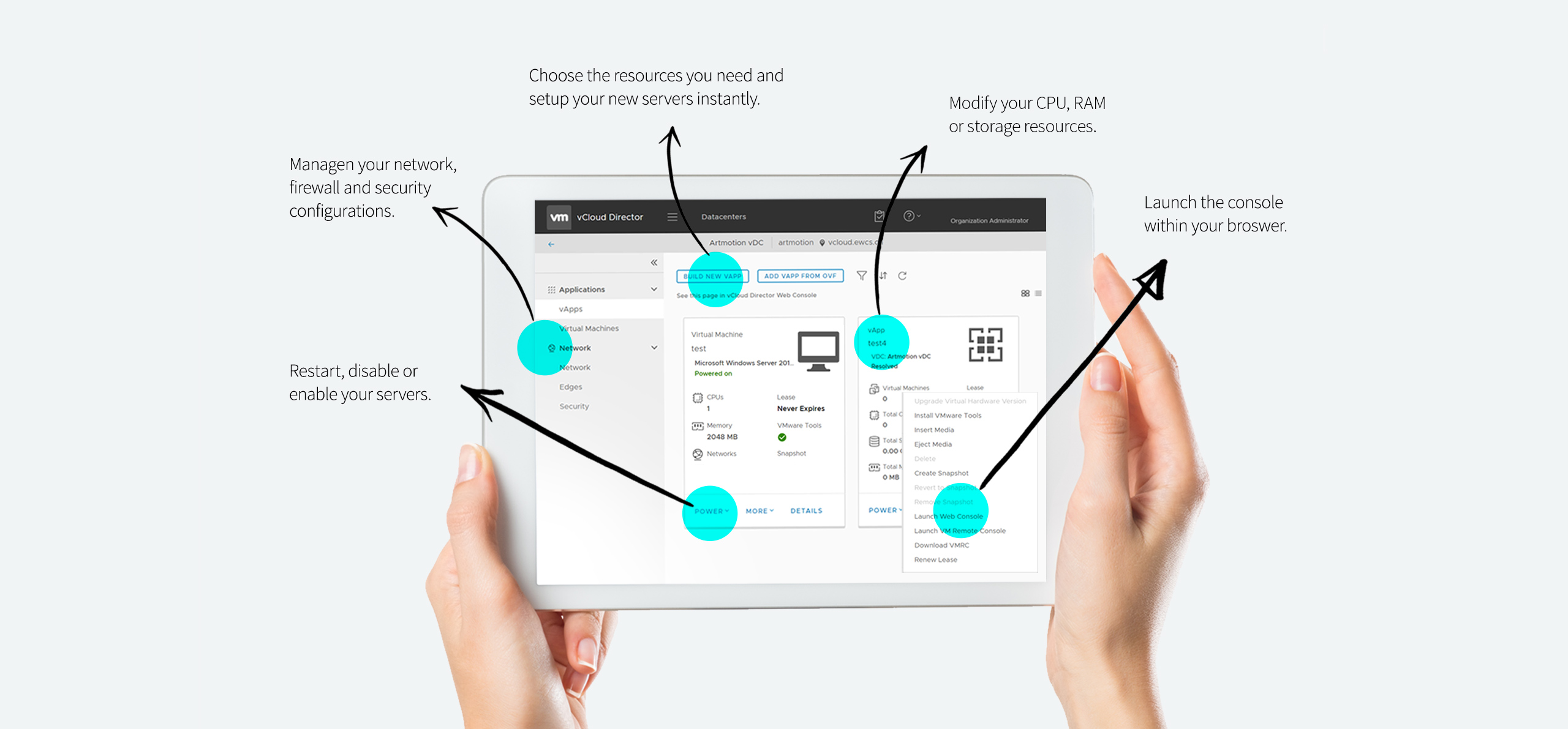
Why VMware Cloud?
With the self-service web portal of VMware vCloud Director, you can manage your private cloud infrastructure in minutes.
The following functions are available within the interface:
- Create or remove virtual servers
- Expand resources
- Reboot virtual servers
- Get access to the console
- Mount any ISO files
Test our vmware vCloud Director interface for free now.
Creating a Snapshot preserves the state and data of a virtual machine at a specific point in time. You can create a Snapshot or restore a snapshot at any time.
Configure DHCP, NAT, Firewall Services, Routing, and DNS.
The firewall helps you effectively meet key security requirements, such as building DMZs, configuring tenant-to-tenant isolation, adjusting NAT, routing, VPNs, or DNS configurations.
Make your servers highly redundant by relying on load balancing engines.
We support two load balancing engines, which you will manage and configure yourself. The layer four load balancer is packet-based and provides fast-path processing. The load balancing engines based on layer seven, which is a is a socket-based solution, supports advanced traffic management strategies.
View Tasks and Events, Manage Blocking Tasks and View Usage Information of your infrastructure and your VMs.
We support the following operating systems:
Microsoft Windows Server 2016
Microsoft Windows Server 2012
CentOS
Run your VM on any OS by mounting your own ISO.
All your servers are automatically encrypted (AES 256-BIT XTS) per default.
Pricing calculator
Calculate the cost of your new virtual data center
The cost of your virtual Swiss datacenter will depend on your specific requirements. By using the pricing calculator below, you can estimate the cost of your new virtual data center. We will provide you with full admin intreface, which is based on vmware vCloud Director. Get your 150 Euro - 15 days free access now and start deploying new servers instantly!
Got specific questions on VMware vCloud Director, vSphere or vCenter from VMware ?
1. Your web interface
The user interfaced is equipped with a variety of tools that will help you configure your virtual IT infrastructure exactly how you want it. You can do this from anywhere in the world with just a few clicks.
2. Encryption layer
All the data at rest that flows into our servers will be encrypted with our proven military-grade encryptors that meet secure network performance demands for real-time, low latency, and robust security without compromise.
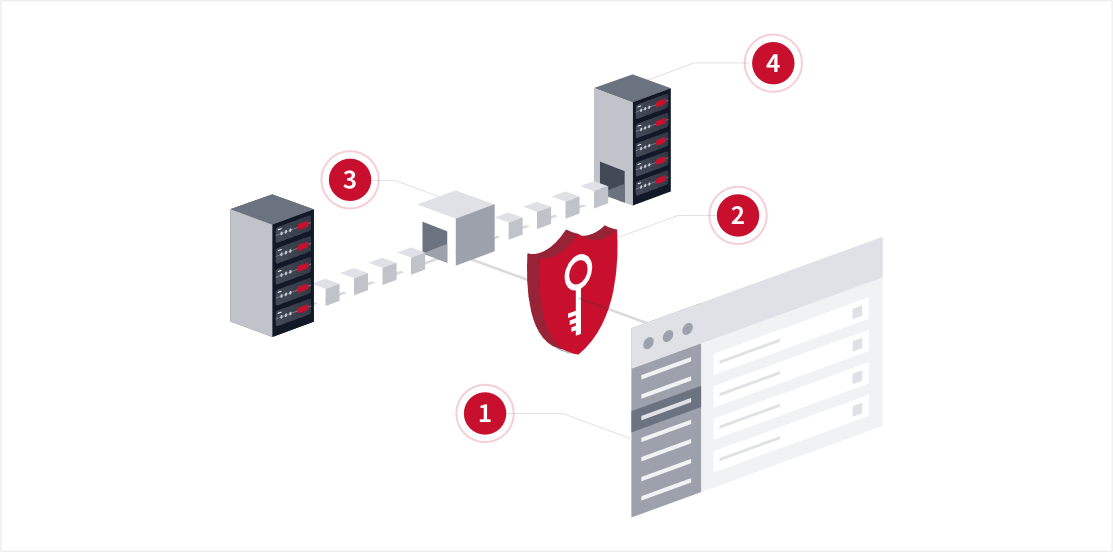
3. Data Slicer
The encrypted data that is stored in our data center is sliced into multiple pieces to enhance and optimize privacy and security protocols.
4. Distrubution to different location
The sliced data is then distributed to different locations to make unauthorized access extremely difficult.
Why do we encrypt the data?
We do this because hackers try to steal trade secrets, disrupt business continuity with ransomware attacks, and compromise customer data. This is why we prefer to store your sensitive information in several locations by breaking up your data and spreading them across multiple nodes. Each storage group will be encrypted with its own private key.
As a result, it will be impossible for any other node that is participating in the network to look at the file. This process is known as "sharding." When we engage in sharding, it ensures that the files are just a fraction of their original self. This means that it will make it impossible for anyone without authorized access to read the entire content.