Trust no one: how zero trust secures enterprise networks
Data breaches are now the norm. This makes it critical for companies to deploy a zero trust framework to secure enterprise networks.
Traditional approaches to enterprise security don’t work. The current threat landscape requires businesses to adopt a variety of cutting-edge tools and technologies to avert a potential data breach.
The Marriott Hotels, for example, can’t seem to keep their brand out of the headlines. The hotel chain, which was already the victim of one of the biggest data breaches in history, fell victim to another within two years, exposing the personal information of about 5.2 million guests.
While the reasons remain unclear, their security protocols were obviously not up to the mark. For years, companies have relied on traditional networking security models that are no longer effective. In this scenario, if you add franchises and third-party vendors to the network, you’re asking for trouble.
However, when companies add a zero trust model, they’re better-placed to securing all access to enterprise applications, environments, and networks. But before we get any further, let’s define it.
What’s zero trust?
Zero trust is a security framework that’s based on the idea that organizations shouldn’t trust anyone. For example, if access attempts originate from inside or outside enterprise perimeters, protocols are implemented to verify any attempt to connect to the network before granting access.
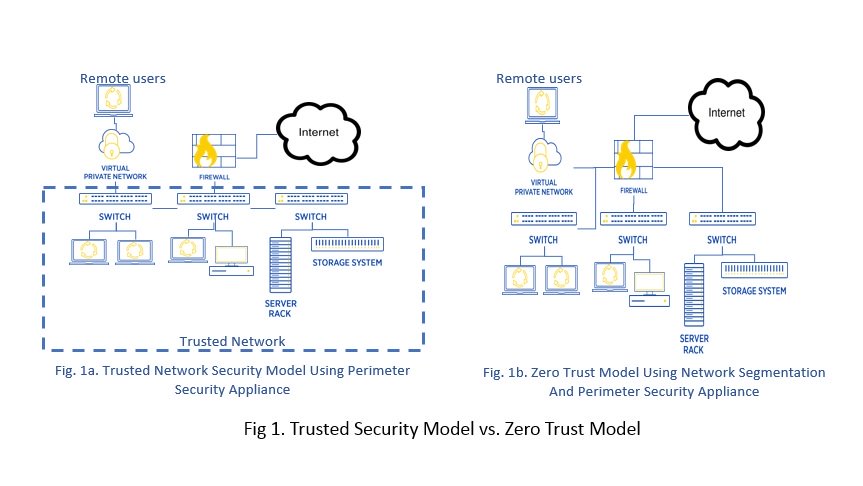
(Source: CloudTech).
If you look at Figure 1, you’ll notice that the traditional security model is a bit like an airport. Before you can head to the boarding gates, you need to first go through airport security.
In this scenario, for example, an officer will check your ID/passport, travel documents, and scan your luggage and your person for prohibited items. Once you clear immigration/security, you're free to wander around most parts of the airport, including other terminals, even if your flight gate is far from that location.
However, with zero trust, you will be restricted to walking to your boarding gate. If you attempt to veer off track, you'll be stopped by airport security.
Getting back to enterprise networks, zero trust is a design that deploys micro-perimeters around specific data or assets. In this scenario, more-granular rules can be enforced to prevent unauthorized access, contain breaches, and minimize the risk of a hacker's lateral movement through your network.
You can say it’s a security framework that also solves the “flat network” issue that allows threat actors to move around corporate networks undetected.
The zero trust framework also provides access for employees no matter where they’re connecting from but with predefined defensive layers. This approach is ideal for the current Work From Home initiatives brought on by the COVID-19 pandemic.
How does zero trust work?
When you enforce a zero trust approach on your network, you always assume that the network is under attack or that something suspicious is going on. Furthermore, you also believe that there are still multiple internal and external threats to the network.
Every user, device, and application on the enterprise network is supported by strong identity authentication (or user verification via authentication) before awarding access. In this scenario, network locality doesn’t automatically equal trust.
Zero trust is also built on the foundation of micro-segmentation. It follows and enforces a “least privileges rule” where staff members are only provided access to areas and information they need to do their job.
You can also add a signal-based approach to add another layer of security. For example, you can analyze the users’ accessibility patterns and determine potential signals for risk. So whenever a user breaks the pattern, you will be alerted to the risk (or threat).
Such events can be the result of working from home and accessing the network in the middle of the night. Or it can be the result of compromised credentials or a hacked device.
The zero trust framework leverages many technologies, including but not limited to:
- Analytics
- Encryption
- Identity and Access Management (IAM)
- Logging
- Network Access Control (NAC)
- Multi-Factor Authentication (MFA)
- Policy enforcement engines
- Policy orchestration
- Role-Based Access Control (RBAC)
- Scoring and file system permissions
Zero trust and encryption
Cybersecurity is an ongoing undertaking. There isn’t a foolproof turnkey solution that businesses can purchase and then forget about. While zero trust will go a long way to secure enterprise networks, you should still take steps to encrypt enterprise data, especially sensitive data like customer information.
For example, the only positive to come out of the 2018 Marriott Hotels data breach (where the details of 383 million guests were stolen) is the fact that the credit card data of 8.6 million customers was encrypted and therefore rendered meaningless to the hackers.
As digital transformation goes through another phase of acceleration (driven by remote working), technology leaders must adopt a strategic approach where security always comes first.
Do you want to secure your cloud infrastructure with zero trust protocols? Request a call back now.