What is extortionware, and how does it work?
In the digital age, crime takes many different forms, including extortion. As such, organizations must take steps to defend against extortionware.
Humanity is generating data at a staggering rate – and that is not stopping anytime soon.
By 2025, our collective data will reach 175 zettabytes. Video streaming, dating apps, health care, and even music contribute to that statistic.
While it is attractive to watch us digitize reality, securing such data is of utmost importance. Organizations are increasingly aware of the consequences that entail an attack.
According to Enterprise Strategy Group’s 2022 Technology Spending Intention Survey, 69% of organizations look to increase their cybersecurity budget in 2022.
The problem, however, is similar to bacterial viruses. Hackers evolve and torment businesses and individuals. Extortionware is one such development, a sickening variant of ransomware.
In this post, we will look at the increasing threat of extortionware, how it is different from ransomware, and what you can do to save yourself a world of trouble.
What is extortionware?
Extortionware is a cyberattack in which the hackers threaten to cause harm if victims fail to meet their demands. Threat actors target industries that deal with sensitive data. Education, medical, and finance sectors are usually first in line.
What is the difference between ransomware and extortionware?
Though the two terms appear interchangeable, ransomware and extortionware have crucial differences.
Threat actors use ransomware to block access by encrypting files in a target database. They then demand payment for restoration, threatening to corrupt data.
Extortionware deals with all sorts of cyber extortion. Once attackers have access, they weaponize sensitive information and make demands.
Example of a ransomware/extortionware attack
Ransomware groups leverage data breaches by using extortionware. For example, Allied Universal, a security services company, faced a data breach in 2019.
The Maze ransomware group was behind this attack. They leaked approximately 700 MB of stolen data. They threatened to leak more data if the company did not pay 300 bitcoin.
The screenshot below shows a few files sent by the Maze actors to Bleeping Computer via email to inform them about the leak. The file names show us their sensitive nature and how seriously damaging they could be if leaked.
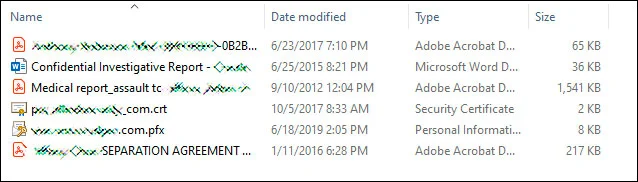
Source: Bleeping Computer.
How to defend against extortionware?
Local backups are crucial to any cybersecurity strategy to defend against ransomware. However, extortionware makes backups obsolete due to the threat of a data leak. Allied Universal had backups, but that did not help because the Maze gang stole the data before it was encrypted.
Once they infiltrate a system, threat actors download the data before encrypting them. So now, it’s not only about recovering your lost data but stopping sensitive information leaks to the public.
Therefore, when combatting extortionware, prevent it before paying millions to keep your data off dark web marketplaces.
Here are the top 6tips to prevent or reduce the impact of such a cyberattack.
1. Update software regularly
Outdated software makes you vulnerable to cyber threats. Software companies continuously fix bugs and weaknesses in their system. It is best to update as soon as a patch or software update is released.
It includes your operating system and other software tools your company uses in its operations.
2. Encrypt sensitive data
When you encrypt your database, hackers won’t know what’s in it even in the event of a data breach.
3. Limit access to sensitive data
Identify and categorize your sensitive data. Protect such data by providing access to authorized employees only with legitimate reasons for data access.
Attackers usually gain access through weak links. Hence, you should vet personnel before authorizing access, maintain audit logs, and consistently monitor for suspicious behavior.
4. Implement and maintain bring your own device (BOYD) security protocols
If your employees bring their own or personal devices to work, you need to be extra careful. Personal devices are usually less secure than corporate devices. Therefore, it’s important to regulate BYOD security protocols in organizations (regardless of size).
5. Restrict remote access
Like BYOD practices, work-from-home also poses potential threats. Personal or remote networks are far less secure compared to enterprise networks.
If there is no choice other than allowing employees to work remotely, do so after providing maximum protection. Otherwise, restrict remote access to servers to reduce the risks of a breach.
6. Conduct regular cyber hygiene workshops
Employee cybersecurity hygiene will help avert unwanted and unforeseen trouble. Everyone in your organization is not tech-savvy, and not everyone is alert to a social engineering campaign. Train all employees, and encourage them to learn about your cybersecurity policies and protocols. They should not say, “I thought I really won the lottery,” after clicking on a malicious link.
Train them to:
- Use strong passwords
- Be extra vigilant when opening emails
- Update software regularly
- Monitor and notify suspicious behavior
Cybersecurity best practices are there for a reason. It is not a negotiable habit, so make sure to follow, re-visit and strengthen your security policies.
Cybercriminals are getting creative. They leverage data and exploit vulnerable networks for money. Ransomware-as-a-service is also available on the dark web, opening the door for criminals who aren’t exactly tech-savvy.
Anyone can use the service, not just ransomware gangs. Remember, just because you pay them once does not mean they will not threaten you again. Take steps to defend against extortionware attacks and keep your sensitive data away from the dark web.